Rails Vulnerability Scanning and Static Analysis
Tuesday, 2 December 2014 · 4 min read · rails
Static program analysis is the analysis of computer software that is performed without actually executing programs (analysis performed on executing programs is known as dynamic analysis). The term is usually applied to the analysis performed by an automated tool, with human analysis being called program understanding, program comprehension, or code review. – More on Static Analysis
Have you ever wondered how QA services such as Codeclimate and New Relic measures your code quality? They use the Brakeman static analyser.
Brakeman is an open source vulnerability scanner specifically designed for Ruby on Rails applications. It statically analyzes Rails application code to find security issues at any stage of development.
Unlike typical website vulnerability scanners, brakeman scans your source code for vulnerabilities. This means security testing can begin at any stage of development. There is no need for deployment or setting up the full web stack. In fact, your code does not even need to be fully functional.
Using brakeman is as simple as adding the gem into your Gemfile:
group :development do
gem 'brakeman', require: false
endbundle and run brakeman from your app directory! brakeman will start analysing:
Loading scanner...
Processing application in /Users/yosriady/sheethub
Processing gems...
[Notice] Detected Rails 4 application
Processing configuration...
[Notice] Escaping HTML by default
Parsing files...
Processing initializers...
Processing libs...ssed
Processing routes...
Processing templates...
Processing data flow in templates...
Processing models...
Processing controllers...
Processing data flow in controllers...
Indexing call sites...
Running checks in parallel...
- CheckBasicAuth
- CheckCrossSiteScripting
- CheckContentTag
- CheckCreateWith
- CheckDefaultRoutes
- CheckDeserialize
# And so on...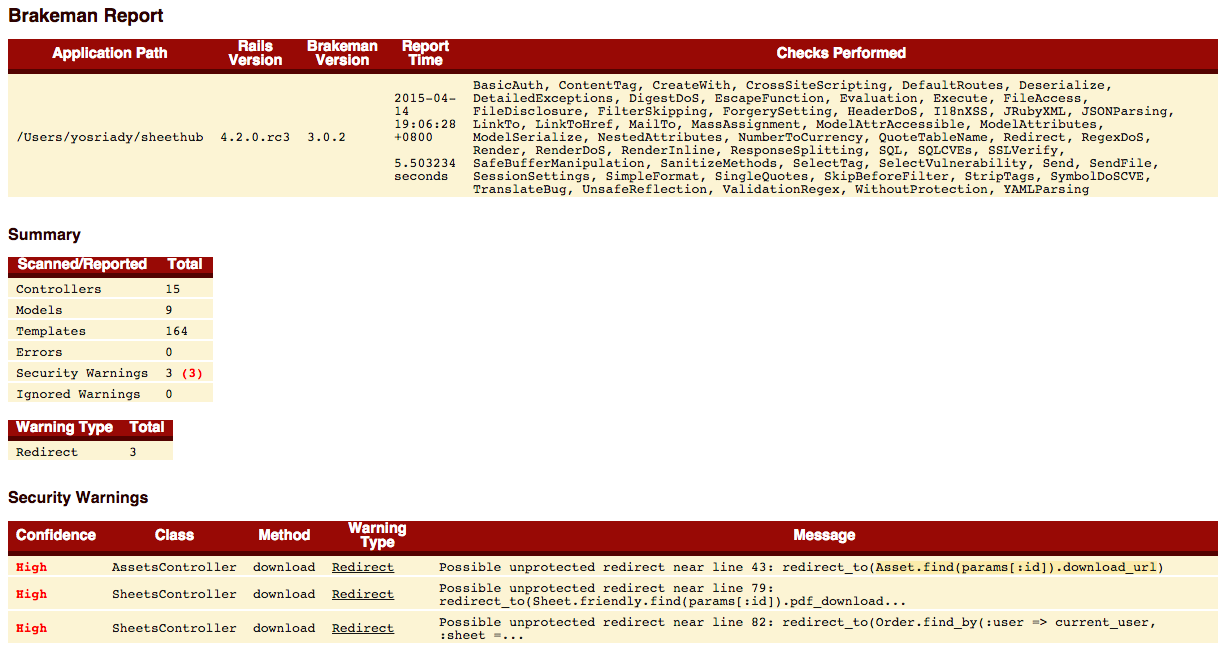
Voila!
Because brakeman does not rely on following links on your website, it can perform a more thorough scan of your application. It is also possible to find vulnerabilities before they are actually exploitable from the live website.
Be sure to check out the project repo. Also check out a number of other security scanners!
Additional Reading:
📬 Get updates straight to your inbox.
Subscribe to my newsletter so you don't miss new content.