‘Smart contracts’ is a misnomer. Despite its name, smart contracts on Ethereum are not self-executing digital agreements. Smart contract code only run when triggered by an external account. In other words, you need an external process to trigger the smart contract.
In this article, we’ll build a solution to this problem. You’ll learn:
- Why you need off-chain smart contract automation
- Use cases for smart contract automation
- How to deploy serverless functions with the Serverless framework
Finally, we’ll go through serverless-ethers, a fully-functional smart contract automation service that you can run and deploy out-of-the box! Feel free to use this project as a base for building custom smart contract automation that fit your needs.
The serverless-ethers sample application is open source and available on Github. Just clone and hit deploy! 🚀
Read on to learn why we need automation and how it works.
Continue reading →

Recently is a periodic retrospective.
At the end of a month I publish a review of things I read/wrote/built/thought over the past month. My goal is to create a ‘brain log’ where I can capture these ideas on paper for future me to review.
Continue reading →

This is an abridged explanation of how money emerged from an initial state of barter. Most of the material is from the book Choice: Cooperation, Enterprise, and Human Action by Robert Murphy.
Murphy’s book reviews the works of Ludwig von Mises’ Human Action and Carl Menger’s On the Origins of Money. I highly recommend checking them out if you find the following summary interesting.
Continue reading →
This is an abridged version of Jörg Guido Hülsmann’s The Ethics of Money Production, with an emphasis on the origins of money, private coinage, and competition of private currencies.
The original book is available as a free PDF and on paperback. Images used are from Spice and Wolf by Keito Koume and Isuna Hasekura.
Continue reading →

This is an abridged version of Friedrich Hayek’s The Use of Knowledge in Society.
Continue reading →

While you live, shine
have no grief at all
life exists only for a short while
and time demands its toll.
— The Seikilos Epitaph (Listen)

Decentralized Finance (or DeFi) is an emerging category of financial applications that are being developed on top of trustless networks. Today, most of this innovation is happening on the Ethereum blockchain. An entire digital finance stack came into existence within the past 18 months, under the radar of most people.
This guide will explain to you what DeFi is all about, without the jargon.

Our exploration of DeFi will consist of three parts:
-
An introduction to what DeFi means and why it matters.
-
A tour of different financial applications in the Ethereum ecosystem.
-
A deep dive into decentralized lending with the Compound protocol.
By the end of this guide, you’ll have a better understanding of DeFi and be able to learn more on your own. Read on!
Continue reading →

The history of software development spans decades. We benefit from the best practices, design patterns, and nuggets of wisdom that has accumulated over half a century.
In contrast, smart contract development is just getting started. Ethereum and Solidity launched in 2015, only a handful of years ago.
The crypto space is an ever-growing uncharted territory. There’s no definitive stack of tools to build decentralized apps. There are no developer handbooks like Design Patterns or Clean Code for smart contracts. Information about tools and best practices are scattered all over the place.
You’re reading the missing guide I wish existed. It summarizes the lessons I’ve learned from writing smart contracts, building decentralized applications, and open source projects in the Ethereum ecosystem.
Continue reading →
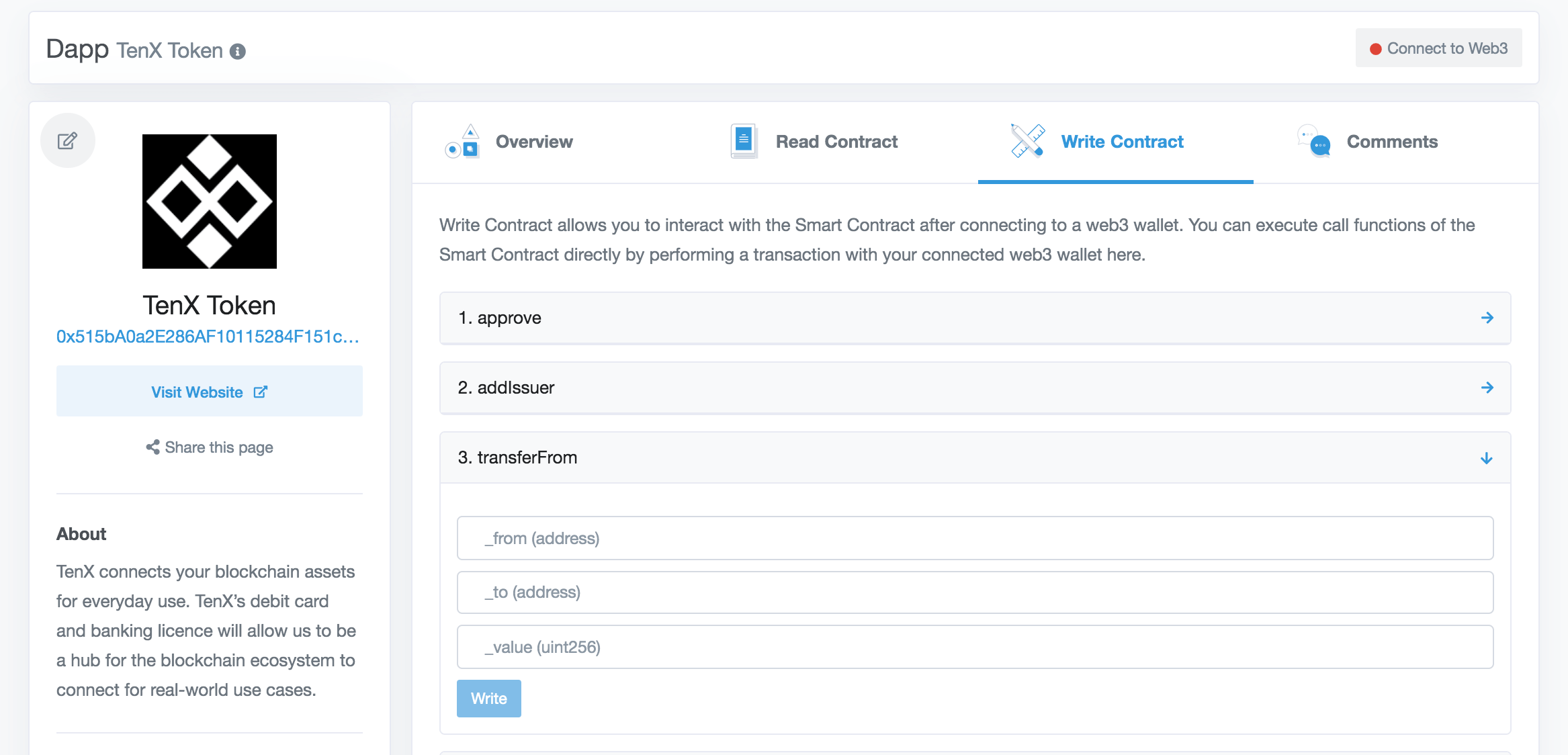
Do you need to quickly build a web UI for your smart contracts?
Etherscan can do that for you! Read on to learn how to verify your Solidity smart contracts on Etherscan.
Continue reading →
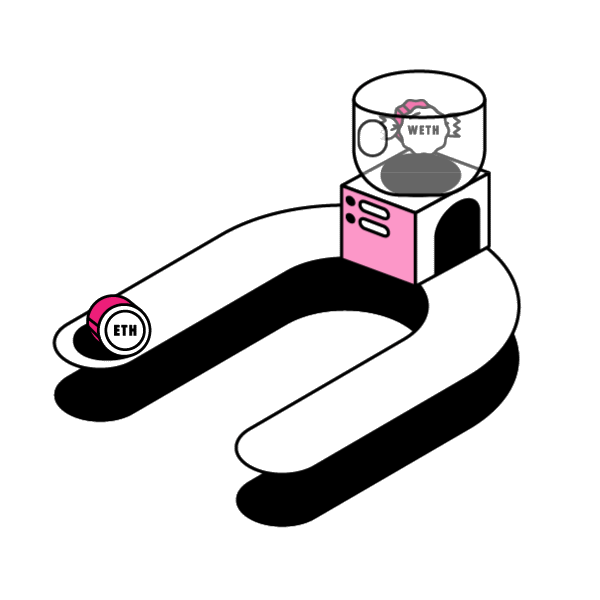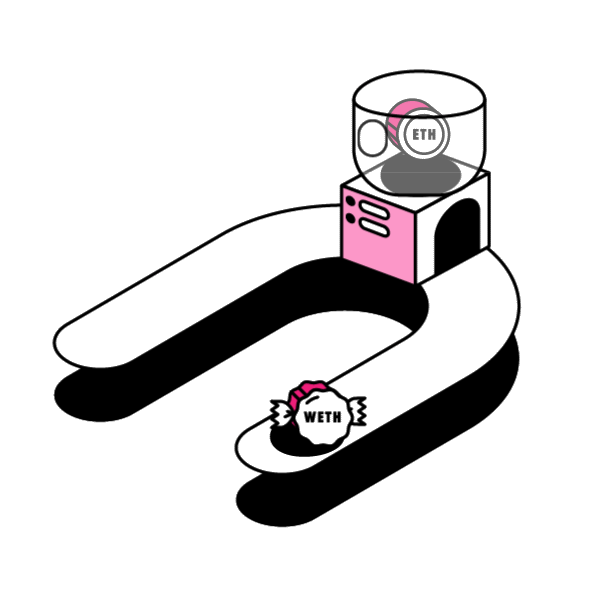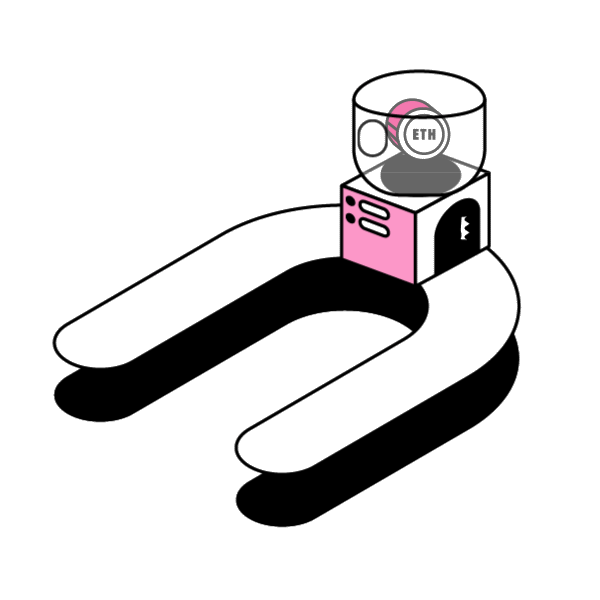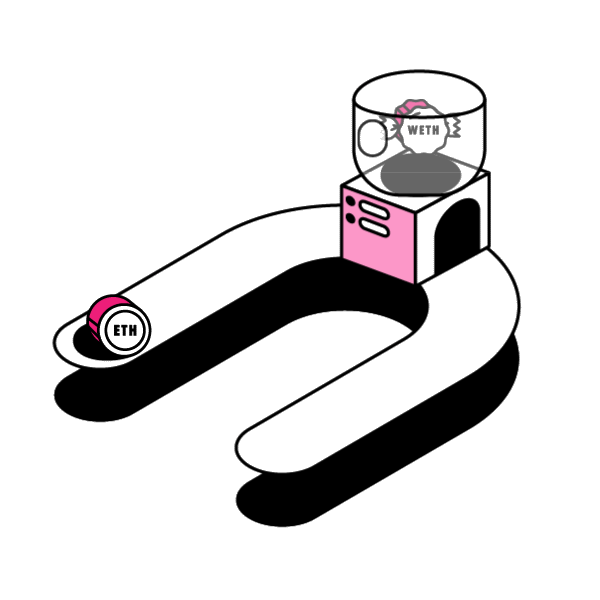
Smart contracts’ open source and immutable nature enables permissionless innovation in the space. People and companies can innovate on top of protocols without worrying about the rules of the game changing later on. Any Developer can innovate and build new dApps freely in a permissionless manner, without needing anybody’s approval.
When a dApp (decentralized app) is built off of the Ethereum Blockchain it usually implements its own ERC20 Token. Think Augur’s REP Token, or Bancor’s BNT Token. ERC20 is a token standard developed after the release of ETH that defines how tokens are transferred and how to keep a consistent record of those transfers among tokens in the Ethereum Network.
Decentralized services can be composed together to harness their particular strengths. The question is: How can developers extend the capability of an existing ERC20 token contract? In this article, let’s examine a design pattern around smart contract extensibility: Wrapped Tokens.
Continue reading →










